What Function Describes the Use of an Access Control List
In this article we will go deep into the functionality of ACLs and answer the following common questions about ACLs. Access control lists are also installed in routers or switches where they act as filters managing which traffic can access the network.

What Is Access Control List Acl Types Linux Vs Windows Imperva
ACLs provide a basic level of security for network access.

. 5 ACLs can permit or deny traffic based upon the MAC address originating on the router. They let us tack on access for other users or groups. ACLs provide a basic level of security for network access.
C ACLs assist the. ACLs can permit or deny traffic based upon the MAC address originating on the router. ACLs can be used to filter private IP addresses.
ACLs control which user can access what services on the Internet. ACLs can permit or deny traffic based upon the MAC address originating on the router. Similarly to create an extended IP access list you can select any number between 100-199 and 2000-2699.
Standard ACLs can restrict access to specific applications and ports. You can configure access control lists ACLs for all routed network protocols IP AppleTalk and so on to filter protocol packets when these packets pass through a device. The SetEntriesInAcl function uses an array of EXPLICIT_ACCESS structures to specify the information for the new ACEs.
An Access Control Lists ACL is a function that watches incoming and outgoing traffic and compares it with a set of defined statements. Extended ACL An access-list that is widely used as it can differentiate IP traffic. An access control list ACL is a list of rules that specifies which users or systems are granted or denied access to a particular object or system resource.
Access-Lists ACL Difficulty Level. Each entry in an access control list specifies the subject. 2 ACLs can permit or deny traffic based upon the MAC address originating on the router.
TCO 6 What function describes the use of an access control list. This type of situation is what Linux Access Control Lists ACLs were intended to resolve. Examples include IP IPX ICMP TCP UDP NETBIOS and many others.
Key concepts that make up access control are permissions ownership of objects inheritance of permissions user rights and object auditing. Choose two a ACLs can control which areas a host can access on a network. Access-list ACL is a set of rules defined for controlling network traffic and reducing network attacks.
Choose two ACLs can control which areas a host can access on a network. Cisco provides basic traffic filtering capabilities with access control lists also referred to as access lists. Each EXPLICIT_ACCESS structure contains information that describes a single ACE.
What two functions describe uses of an access control list. One of the most important functions of access control lists is the ability to prevent unauthorized users from accessing sensitive. ACLs containts a list of conditions that categorize packets and help you determine when to allow or deny network traffic.
TCO 6 What function describes the use of an access control list. ACLs allow us to apply a more specific set of permissions to a file or directory without necessarily changing the base ownership and permissions. ACLs assist the router in determining the best path to a destination.
Choose two ACLs assist the router in determining the best path to a destination. Where Can You Place An ACL. 5 ACLs can permit or deny traffic based upon the MAC address originating on the router.
Standard ACLs can restrict access to specific applications and ports. What two functions describe uses of an access control list. ACLs provide a basic level of security for network access.
They dont differentiate between IP traffic such as UDP TCP and HTTPS. What two functions describe uses of an access control list. Access Functions by category Access for Microsoft 365 Access 2021 Access 2019 Access 2016 Access 2013 Access 2010 Access 2007 More.
Access control list ACL refers to the permissions attached to an object that specify which users are granted access to that object and the operations it is allowed to perform. ACLs provide assurance that no attacks occur on the network. ACLs are used to filter traffic based on the set of rules defined for.
It is always preferred to use Extended ACLs since they are more flexible. Extended ACLs must be applied in egress interfaces to lower CPU utilization. TCO 6 What function describes the use of an access control list.
What are two possible uses of access control lists in an enterprise network. Standard ACLs can restrict access to specific applications and ports. An Access Control List ACL is a set of rules that is usually used to filter network trafficACLs can be configured on network devices with packet filtering capatibilites such as routers and firewalls.
This information includes the access rights the type of ACE the flags that control ACE inheritance and a TRUSTEE structure that identifies the. These access control lists allow or block the entire protocol suite. Below are some additional reasons why a company might use access control lists.
What are two uses of an access control list. This topic for the IT professional describes access control in Windows which is the process of authorizing users groups and computers to access objects on the network or computer. To create an IP access list you must specify a number from the above pre-defined number ranges.
A network protocol and associated function or ports. TCO 6 What function describes the use of an access control list. For example to create a standard IP access list you can choose any number between 1-99 and 1300-1999.
ACLs should always be placed close to the source to avoid waste of computing resources. Windows Server 2016. Access Control List Overview and Guidelines.
Standard ACLs can restrict access to specific applications and ports. A statement of permission or denial for that entry. We can view the current ACL using the getfacl command.
B ACLs can permit or deny traffic based upon the MAC address originating on the router. Choose two ACLs assist the router in determining the best path to a destination. Standard ACLs can restrict access to specific applications and ports.
This article contains links to articles that provide details about common functions used in expressions in Microsoft Access. ACLs can control which areas a host can access on a network. ACLs provide assurance that no attacks occur on the network.
Extended ACLs must be applied in egress interfaces to lower CPU utilization. Why Use An ACL. They use numbers 1-99 or 1300-1999 so the router can recognize the address as the source IP address.
Question 1 TCO 6 What function describes the use of an access control list. Access control lists in networking offer privacy security and simplicity for large corporations that house large amounts of data. What is an Access Control List.
Access control list name depending on the router it could be numeric or combination of letters and numbers A sequence number or term name for each entry. What two functions describe uses of an access control list.
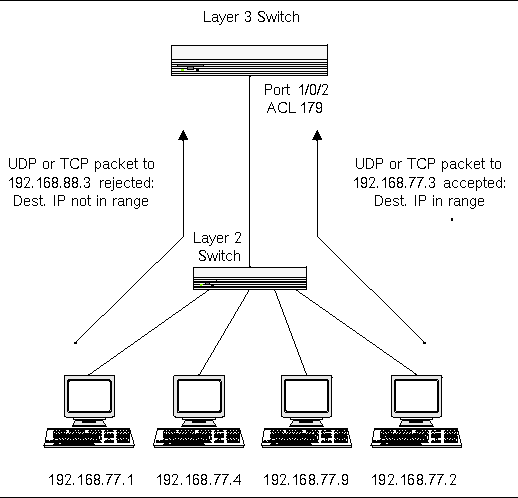
Configuring Access Control Lists Acls

Comments
Post a Comment